Note: This content was originally published at the Simple AWS newsletter. Understand the Why behind AWS Solutions. Subscribe for free! 3000 engineers and tech experts already have.
AWS Systems Manager is a service that helps you manage fleets of EC2 instances. Session Manager is a capability of Systems Manager, which lets you connect through SSH to EC2 instances without needing SSH keys.
Once it's set up, you can use Session Manager to SSH into an EC2 instance with just two clicks, directly from the AWS EC2 console, and with no SSH keys. You can also use it directly from you command line interface with the AWS CLI.
Features of Session Manager
Session Manager's job is simple: it lets IAM users SSH into EC2 instances. It comes with several features to help you manage who can use it and how:
Limit who has access to what instances
Permissions to use Session Manager are IAM permissions associated with IAM Users or Roles. This lets you create policies that grant the permission to start a Session Manager session for only certain resources, like EC2 instances with tag "Development". You can then associate these IAM policies with the corresponding IAM Users or IAM Roles, to grant only certain people the ability to use Session Manager, and only with the specified resources (EC2 instances).
You can also include additional restrictions in the IAM Policy, such as the source IP of the request being in certain range, or the IAM User having authenticated with MFA.
Monitor and alert on session start
Every time Session Manager starts a new session, an event is fired, which is automatically sent to EventBridge and logged in CloudTrail. You can use the CloudTrail event history to view who started a session, when, and on what resource.
You can also create a rule in EventBridge to send session start events to an SNS topic, which can in turn notify you via email when a session is started. If you haven't set up Organizations and are running a production environment in the same account as other environments, you could filter the event by which instance is being SSHed into.
Log every command and output used on the session
Session Manager can be connected to CloudWatch Logs, and it can either send logs of the entire session when it's closed, or continuously stream session logs in real time. This can be used for later review and archival purposes, or you can scan them in real time to detect certain commands ran in your EC2 instances.
Using CloudWatch Metrics, you can generate metrics on how many times some commands are run. With CloudWatch Alerts you can get alerted via email if the execution of some command exceeds a threshold, or even trigger automated responses such as terminating a session and removing a user's permissions to use Session Manager.
Session Manager also lets you view every session initiated on your EC2 instances over the last 30 days, including the user that initiated it and the timestamp when it happened.
Limit commands that can be used in the SSH session
By default, Session Manager allows users to use any command. However, you can limit the commands that users can run using Session Manager. These limitations are per IAM User that has access to Session Manager, so you could have some people be able to run a command such as sudo su, and make others unable to run the same command on the same instances.
Forward a connection to a database or remote host
Session Manager lets you initiate an SSH connection that jumps through an instance managed by Session Manager, and is forwarded to another instance or database. This lets you create jump hosts (also known as bastion hosts) that are managed by Session Manager, and which you use to connect to another destination such as a database instance without a public IP address, but which is accessible from the jump host.
The destination doesn't need to be managed by Session Manager, it just needs to be accessible from the instance you're connecting through. You can use this for SSH connections, database connections, or anything that could be done from the instance managed by Session Manager.
Benefits of using Session Manager instead of SSH keys
These are the key benefits of using Session Manager:
No need to share or rotate SSH keys
With Session Manager, you don't use SSH keys anymore. If you want someone to be able to SSH into an EC2 instance, you grant their IAM or IAM Identity Center user permissions to use Session Manager, and they can connect with no changes on their end.
If you want to remove access to a particular person, you remove their IAM permissions, without affecting any other users. If you were using SSH keys, you'd have to rotate the SSH key used for that instance, and share it with every other person that accesses the instance. Session Manager makes it much easier.
No need for ports open to the internet
Session Manager doesn't require you to open port 22 to all IP addresses on the instances' Security Groups. This eliminates a vulnerability where anyone could potentially attempt to connect to your instances over that port.
No need to have a public IP address
Instances don't need a public IP address or access to the internet to be accessible from Session Manager. They will need a VPC Endpoint so they can connect to Session Manager, but that happens over the instance's private IP address, and doesn't expose the instance to any other types of connections. This way, instances behind load balancers have no reason to use public IP addresses anymore, which is both a much better security posture, and will be relevant for costs once AWS starts charging $3.6/month per public IPv4 address in use.
No need for a bastion host
Bastion hosts are typically used so you only expose one instance to the internet, and use it to jump to other instances in the private network. Their key benefits are that you only install SSH keys in one instance, and that you only harden one instance against attempts from malicious actors. By removing the need for SSH keys and removing all public access to your instances, you no longer need to jump the connection through a bastion host.
How to set up AWS Session Manager
Step by step instructions to configure Session Manager
Make sure the instance is managed by Systems Manager. Here's how to set that up.
-
Ensure the instance has permissions to use Session Manager. Here's two ways to add these permissions, you can follow either one:
- Attach the AmazonSSMManagedInstanceCore IAM Policy to the instance's associated IAM Role
- Follow this guide to create your own policy
Make sure the SSM agent is installed on the instance. It's installed by default on most EC2 AMIs, but just in case, here's how to install it for Linux, Windows and macOS
-
Make sure the instance has HTTPS (port 443) access to these endpoints (this can be done via internet access or with a VPC Endpoint):
- ec2messages.region.amazonaws.com
- ssm.region.amazonaws.com
- ssmmessages.region.amazonaws.com
- kms.region.amazonaws.com if you want to encrypt sessions
- logs.region.amazonaws.com to send session logs to CloudWatch Logs
- s3.region.amazonaws.com to send session logs to S3
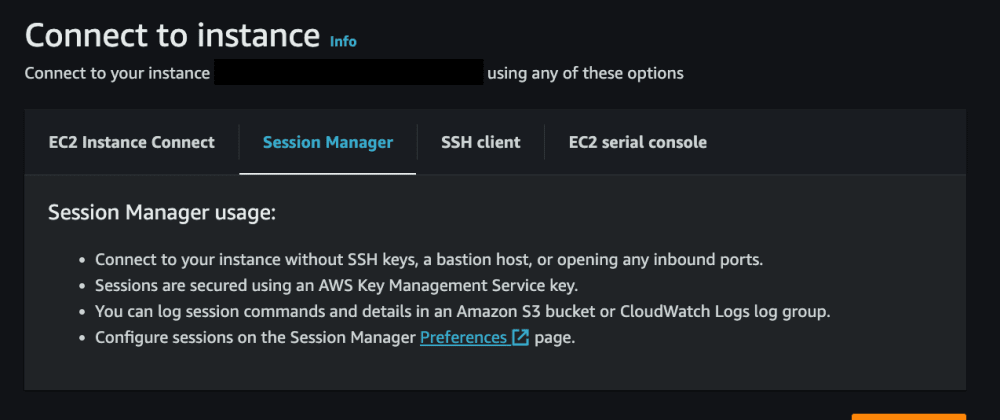
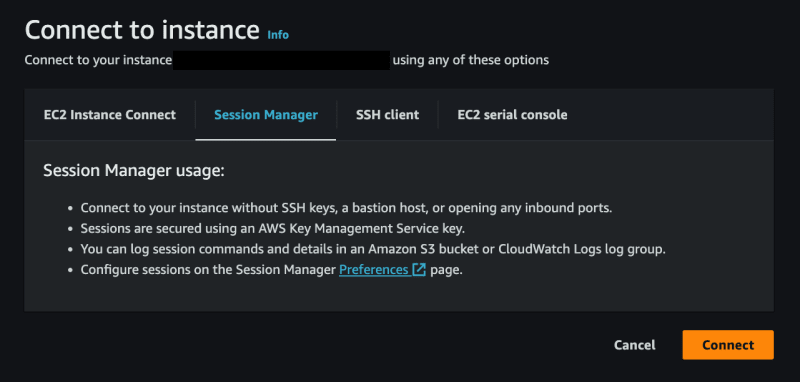
How to start a session with Session Manager
To start a session from the console:
Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/
In the navigation panel on the left, click Instances
Select the instance you want to connect to
Click Connect
Go to the Session Manager tab
Click Connect
To start a session from the CLI, use the following command, replacing {INSTANCE_ID} with the ID of the instance you're trying to connect to:
aws ssm start-session --target {INSTANCE_ID}
For a better experience using the CLI, install the CLI plugin for Session Manager.
Understand the Why behind AWS Solutions.
Join over 3000 devs, tech leads, and experts learning how to architect cloud solutions, not pass exams, with the Simple AWS newsletter.
- Real-world scenarios
- The Why behind solutions
- How to apply best practices
If you'd like to know more about me, you can find me on LinkedIn or at www.guilleojeda.com






Top comments (0)